
This article provides a brief introduction to the data-driven, process-discovery technique called process mining. It compares traditional process modeling based on interviews and workshops with process mining. The authors also seek feedback to help understand the current perceptions of process mining.
What is process mining?
For any process-improvement project, understanding the current state, usually via as-is process models, is important. Stakeholders are interviewed, existing documents are reviewed, and a process model is created using a modeling tool. Such process models are mostly based on stakeholder perceptions of the process. This can be a good approach, possibly the only approach, for processes that are mostly manual. However, with increasing IT system involvement in process execution, there is a wealth of information recorded in various system or event logs. These traces present the facts—that is, evidence of real events that have happened or, in other words, the real as-is. Process mining creates a process model from the data in the traces or event logs, and this represents the current-state operation that is based, not on perceptions, but on hard evidence of what actually has happened.
Using event logs maintained by information systems, the real-life process flow—with all of its possible paths, including exceptions and escalations—can be visualized using specialized process mining software. The generated process flow allows detailed analysis of the current state. Process mining is about visualizing the as-is process; it is an aid to analysis, but the process mining tool does not provide solutions or to-be processes.
There are many possible process mining use cases. Three scenarios are described below.
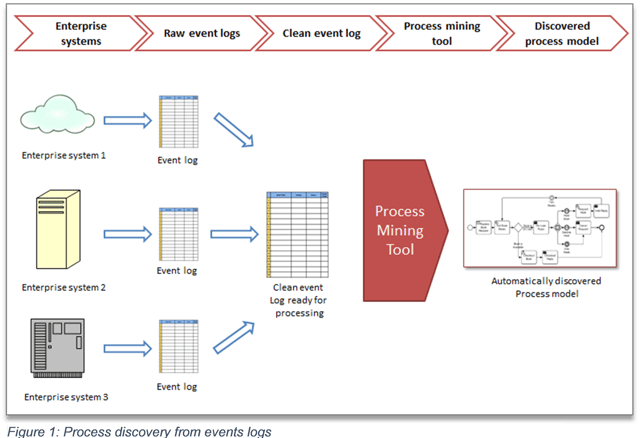
Scenario 1: Process discovery from event logs
The first use case, illustrated in Figure 1, focuses on process discovery. Event logs are extracted and made ready for mining—that is, the data is cleaned and reformatted for a process-mining tool. The process flows generated by process-mining tools are more reliable than those created by interviewing process stakeholders. The event logs reveal the real process, rather than how it’s perceived by its actors. Exception scenarios (most likely neglected in interviews) can be discovered, and overall process performance is highlighted. This process-discovery scenario provides data for future process analysis and improvement, and a basis for further analysis, such as process compliance, or a prediction of process paths based on historical data.
 Imagine a customer-care center. A customer registers a complaint; the system then records the details as a ‘case’, and the customer-care agents work to resolve the case—writing comments, involving different teams as required and, finally, closing the case. Customers have complained that, every other day, different agents call them to ask for more details, but nothing happens after that. Process mining can read the logs for each case, and then visually display the process in as much detail as required. This will discover the ‘real’ process and show what is actually done (and what is not done). This information can be used for further analysis
Imagine a customer-care center. A customer registers a complaint; the system then records the details as a ‘case’, and the customer-care agents work to resolve the case—writing comments, involving different teams as required and, finally, closing the case. Customers have complained that, every other day, different agents call them to ask for more details, but nothing happens after that. Process mining can read the logs for each case, and then visually display the process in as much detail as required. This will discover the ‘real’ process and show what is actually done (and what is not done). This information can be used for further analysis
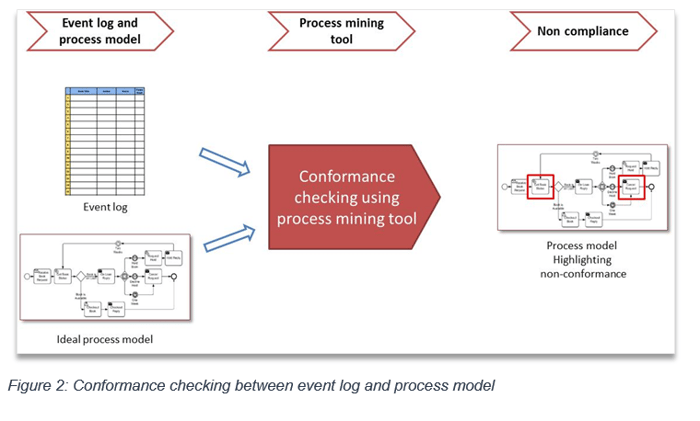
Scenario 2: Process conformance check
The second scenario, illustrated in Figure 2, focuses on process conformance checks, where event logs are checked against the ideal process. The ideal process could be an improved and optimized version of the process outcome of scenario 1 (process discovery). It could also be an independently designed process. The process mining tool converts event log files into a process model, and then checks this real-life process model against the ideal. Mismatches between the process model derived from event logs and the ideal process are diagnosed, and non-conformances highlighted and visualized—this allows these process parts to be further analyzed and optimized.
For example, every company needs to maintain accounts using fixed processes for capturing financial transactions. Auditors benefit from using a process-driven approach by using process-mining methods to highlight deviations from accounting standards. Once real process non-compliance is highlighted, the deviations are the subject of further analysis and improvement.
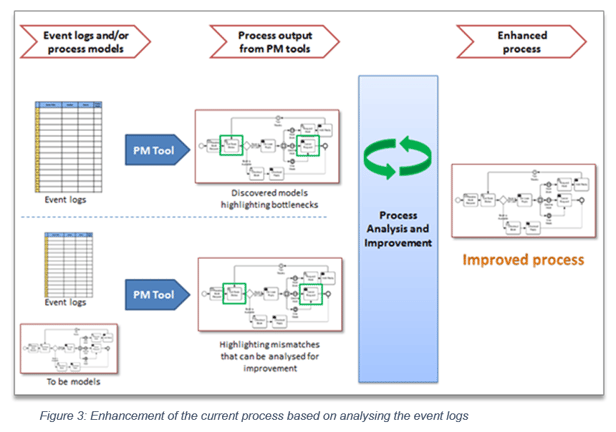
Scenario 3: Process enhancements
The third scenario (see Figure 3) focuses on process enhancement, where event logs are analyzed to enhance or improve a process. It starts with process discovery, followed by process evaluation and optimization—then, various performance parameters of a process are analyzed to improve the process performance. An ideal process model could also be used within this enhanced process to identify and highlight mismatches.
For example, in order processing, the process steps representing the bottlenecks can be precisely highlighted. This is very similar to process simulation, but uses actual transaction data that is seldom used by simulation. If we discover that the ‘order review’ is taking the most time, we will then do further analysis. Process change will be based on the reality that is represented by event logs in the system.
Summary
Process mining can provide useful insights that facilitate improvement in process performance. The deficiencies of interview and workshop-based process discovery can be overcome. In the case of audits, process mining can be used to identify non-conformance. Process mining can be very effectively used to improve and enhance organizational processes.




